Opened 11 years ago
Closed 10 years ago
#10230 closed defect (fixed)
Security warning when starting JOSM on Windows for the first time
| Reported by: | jfd553 | Owned by: | team |
|---|---|---|---|
| Priority: | blocker | Milestone: | 14.07 |
| Component: | Core remotecontrol | Version: | |
| Keywords: | windows https certificate | Cc: |
Description (last modified by )
Automatic update of JOSM through web start ...
Security Warning popup (attached) saying I am about to install a root certificate allowing any further certificates issued by "localhost" being automatically installed...
Is it right? Windows cannot validate that the certificate is actually from the certification authority (CA) localhost? Sounds strange to me...
Repository Root: http://josm.openstreetmap.de/svn Build-Date: 2014-07-03 22:03:52 Last Changed Author: Don-vip Revision: 7287 Repository UUID: 0c6e7542-c601-0410-84e7-c038aed88b3b URL: http://josm.openstreetmap.de/svn/trunk Last Changed Date: 2014-07-04 00:00:19 +0200 (Fri, 04 Jul 2014) Last Changed Rev: 7287 Identification: JOSM/1.5 (7287 en) Windows 7 64-Bit Memory Usage: 53 MB / 247 MB (16 MB allocated, but free) Java version: 1.7.0_55, Oracle Corporation, Java HotSpot(TM) Client VM VM arguments: [-Djava.util.Arrays.useLegacyMergeSort=true, -Djnlp.application.href=http://josm.openstreetmap.de/download/josm.jnlp, -Xbootclasspath/a:C:\Program Files (x86)\Java\jre7\lib\javaws.jar;C:\Program Files (x86)\Java\jre7\lib\deploy.jar;C:\Program Files (x86)\Java\jre7\lib\plugin.jar, -Djnlpx.vmargs=-Djava.util.Arrays.useLegacyMergeSort=true -Djnlp.application.href=http://josm.openstreetmap.de/download/josm.jnlp, -Djnlpx.jvm=<java.home>\bin\javaw.exe, -Djnlpx.splashport=51349, -Djnlpx.home=<java.home>\bin, -Djnlpx.remove=false, -Djnlpx.offline=false, -Djnlpx.relaunch=true, -Djnlpx.session.data=C:\Users\Daniel\AppData\Local\Temp\session865389477705309319, -Djnlpx.heapsize=NULL,NULL, -Djava.security.policy=file:C:\Program Files (x86)\Java\jre7\lib\security\javaws.policy, -DtrustProxy=true, -Xverify:remote, -Dsun.awt.warmup=true] Plugin: PicLayer (30436) Plugin: imageryadjust (30416) Plugin: openstreetbugs (30436) Plugin: turnrestrictions (30454)
Attachments (1)
Change History (19)
by , 11 years ago
| Attachment: | SecurityWarning.png added |
|---|
comment:1 by , 11 years ago
| Keywords: | windows https certificate added; template_report removed |
|---|---|
| Milestone: | → 14.07 |
| Priority: | major → normal |
| Summary: | Security warning → Security warning when starting JOSM on Windows for the first time |
Yes, this is expected behaviour to achieve #10033.
If you click yes, this allows you to use the "Edit" button of osm.org (if accessed in https) to launch JOSM.
I agree it can be frightening at first, so I will probably add another JOSM popup before installing the certificate to explain that better.
comment:2 by , 11 years ago
| Description: | modified (diff) |
|---|
comment:3 by , 11 years ago
| Component: | Core → Core remotecontrol |
|---|
comment:4 by , 11 years ago
The Windows warning sure looks intimidating. Is it really the case, that this certificate can be used to sign another arbitrary certificate, which will be automatically trusted? This would be bad. But I think this is not the case, as the JOSM certificate is not of the CA-type (as far as I can tell):
$ keytool -exportcert -keystore data/josm.keystore -alias josm_localhost -file josmkey.pem -rfc
Enter keystore password:
Certificate stored in file <josmkey.pem>
$ openssl x509 -in josmkey.pem -noout -text
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 17808315 (0x10fbbbb)
Signature Algorithm: sha256WithRSAEncryption
Issuer: O=OpenStreetMap, OU=JOSM, CN=localhost
Validity
Not Before: Jun 1 15:34:45 2014 GMT
Not After : May 31 15:34:45 2019 GMT
Subject: O=OpenStreetMap, OU=JOSM, CN=localhost
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:95:95:88:84:c8:d9:6b:c5:da:0b:69:bf:fc:7e:
b9:96:2c:eb:8f:bc:6e:40:e6:e2:fc:f1:7f:73:a7:
9d:de:c7:88:57:51:84:ed:96:fb:e1:38:ef:08:2b:
f3:c7:c3:5d:fe:f9:51:e6:29:fc:e5:0d:a1:0d:a8:
b4:ae:26:18:19:4d:6c:0c:3b:12:ba:bc:5f:32:b3:
be:9d:17:0d:4d:2f:1a:48:b7:ac:f7:1a:43:01:97:
f4:f8:4c:bb:6a:bc:33:e1:73:1e:86:fb:2e:b1:63:
75:85:dc:82:6c:28:f1:e3:90:63:9d:3d:48:8a:8c:
47:e2:10:0b:ef:91:94:b0:6c:4c:80:76:03:e1:b6:
90:87:d9:ae:f4:8e:e0:9f:e7:3a:2c:2f:21:d4:46:
ba:95:70:a9:5b:20:2a:fa:52:3e:9d:d9:ef:28:c5:
d1:60:89:68:6e:7f:d7:9e:89:4c:eb:4d:d2:c6:f4:
2d:02:5d:da:de:33:fe:c1:7e:de:4f:1f:9b:6e:6f:
0f:66:71:19:e9:43:3c:83:0a:0f:28:21:c8:38:d3:
4e:48:df:d4:99:b5:c6:8d:d4:c1:69:58:79:82:32:
82:d4:86:e2:04:08:63:87:f0:2a:f6:ec:3e:51:0f:
da:b4:67:19:5e:16:02:9f:f1:19:0c:3e:b8:04:49:
07:53
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Alternative Name:
IP Address:127.0.0.1
X509v3 Subject Key Identifier:
39:1C:33:32:30:6A:D6:48:6D:31:BD:45:18:12:61:06:ED:66:CB:41
Signature Algorithm: sha256WithRSAEncryption
70:28:77:da:af:39:ee:af:e3:f3:1d:25:73:0b:5f:eb:72:d2:
fd:b1:96:68:63:24:c5:7f:22:24:55:9f:4c:bf:f5:53:9e:01:
17:a5:3f:a0:d3:ef:49:9d:85:90:81:de:89:b1:5c:4c:fa:ef:
da:00:6a:64:f4:2b:f9:f7:18:09:2c:e3:f6:14:2c:c5:99:98:
8a:81:3c:d5:a8:b9:1c:6b:a6:40:ed:3f:d9:51:19:09:4d:62:
60:1b:56:51:e4:fb:91:9a:bb:e1:b1:2b:ff:6f:67:f3:fe:79:
4e:1e:d2:a9:d8:eb:7e:cb:a0:99:46:31:98:51:94:86:a8:5f:
57:47:e3:6e:42:f3:6b:44:a3:04:3e:bf:ad:77:4d:fe:11:13:
e4:2b:fb:3c:91:0b:7d:64:29:8e:45:55:6f:54:6e:9e:1b:d8:
5a:e4:37:77:89:da:35:75:d1:8a:62:83:5b:67:a4:7e:9c:b1:
2b:29:26:87:cf:2f:d7:5d:43:fa:c5:f2:b7:65:67:ba:63:c0:
65:cc:52:c5:ea:f8:b5:a1:38:17:c7:6f:2d:de:0b:1b:e1:62:
88:70:d5:c6:ba:66:c3:00:18:a3:1f:61:31:bc:f7:e2:a5:14:
9e:9b:a4:fb:d2:5d:b5:3e:dc:fd:30:2a:7f:6e:2f:8a:53:5b:
35:74:ab:d9
It seems that the windows warning is generic, without considering the type of certificate that is installed.
Is it possible to generate a new certificate on the fly on the client computer? The password would be randomly generated, but saved on disk. I think this would significantly reduce any potential security problems as the password is no longer public.
comment:5 by , 11 years ago
| Priority: | normal → blocker |
|---|
I'm not sure it's not a major security risk after all. I need to do this test (try to sign another certificate with our own and see if it gets automatically accepted). Blocker defect for the next tested release.
Concerning your idea of generating the certificate on the fly: yes it was also my idea but I did not find how to generate a certificate without installing a JDK...
follow-up: 7 comment:6 by , 11 years ago
It looks like it's possible: http://bfo.com/blog/2011/03/08/odds_and_ends_creating_a_new_x_509_certificate.html
So I think I can do this:
- if found, uninstall the existing certificate as it may be a huge security risk
- by default, generate and install a new certificate with random password, saved in user settings file. Most users would only have to validate this warning for the first time, but would be able to delete/uninstall the certificate through a new button in remote control preferences
- offer an option to delete/uninstall the certificate during JOSM shutdown. Thus, the certificate would only exist during JOSM session. But this Windows warning will appear each time JOSM is started
comment:7 by , 11 years ago
Replying to Don-vip:
It looks like it's possible: http://bfo.com/blog/2011/03/08/odds_and_ends_creating_a_new_x_509_certificate.html
Great! Just to clarify: This means it is possible to generate a new certificate with a random password directly in JOSM. The question whether the certificate that is currently shipped with JOSM can be used to silently sign other certificates is still open, but it doesn't look like it. Still the publicly distributed private key is sort of ugly and may have consequences we haven't thought of.
In the dialog box that explains the installation, we should have an option "no thanks, not using HTTPS then". Currently the Windows warning is shown at each start if you click decline.
There can be different JOSM preference directories in use at a time (e.g. for latest and tested). This means we'd need to install one for each profile and we'll need some kind of id to distinguish the installed certificates. This is probably a rather unusual setup, so we should aim for the easiest solution that works.
So I think I can do this:
- if found, uninstall the existing certificate as it may be a huge security risk
- by default, generate and install a new certificate with random password, saved in user settings file. Most users would only have to validate this warning for the first time, but would be able to delete/uninstall the certificate through a new button in remote control preferences
Sounds good.
- offer an option to delete/uninstall the certificate during JOSM shutdown. Thus, the certificate would only exist during JOSM session. But this Windows warning will appear each time JOSM is started
I don't think anyone wants that...
follow-up: 12 comment:11 by , 10 years ago
Replying to Don-vip:
- New passwords generated at runtime (but stored in clear in user preferences)
Please, at least use a hash.
comment:12 by , 10 years ago
follow-up: 15 comment:14 by , 10 years ago
Remote control (edit button on osm.org) via https doesn't work for me with Firefox and IE (works with opera though). (I enabled https support in the preferences.)
Also I get the two popups at every josm start, the first to delete the old certificate and the second to install the new one. I this the wanted behavior? It's a bit annoying.
Repository Root: http://josm.openstreetmap.de/svn Build-Date: 2014-07-27 01:35:40 Last Changed Author: Don-vip Revision: 7337 Repository UUID: 0c6e7542-c601-0410-84e7-c038aed88b3b URL: http://josm.openstreetmap.de/svn/trunk Last Changed Date: 2014-07-26 16:36:43 +0200 (Sat, 26 Jul 2014) Last Changed Rev: 7337 Identification: JOSM/1.5 (7337 de) Windows 7 32-Bit Memory Usage: 247 MB / 742 MB (145 MB allocated, but free) Java version: 1.7.0_65, Oracle Corporation, Java HotSpot(TM) Client VM VM arguments: [-Xbootclasspath/a:C:\Program Files\Java\jre7\lib\deploy.jar;C:\Program Files\Java\jre7\lib\javaws.jar;C:\Program Files\Java\jre7\lib\plugin.jar, -Xverify:remote, -Djava.security.policy=file:C:\Program Files\Java\jre7\lib\security\javaws.policy, -DtrustProxy=true, -Djnlpx.home=<java.home>\bin, -Djnlpx.origFilenameArg=C:\Program Files\josm-latest.jnlp, -Djnlpx.remove=true, -Djava.util.Arrays.useLegacyMergeSort=true, -Xms256m, -Xmx768m, -Djnlpx.heapsize=256m,768m, -Djnlpx.splashport=49294, -Djnlpx.jvm=<java.home>\bin\javaw.exe, -Djnlpx.vmargs=LURqYXZhLnV0aWwuQXJyYXlzLnVzZUxlZ2FjeU1lcmdlU29ydD10cnVlAA==]
comment:15 by , 10 years ago
Replying to Klumbumbus:
with Firefox
Yes, and it won't work in this release. In fact I'm not even sure we can make it work without a dedicated plugin because Firefox doesn't use the system certificate store but its own, in a specific format that requires a Mozilla library: NSS/JSS.
and IE
It should work but I have seen it doesn't when accessing 127.0.0.1, that's the address used by OSM website. See my question on StackOverflow fir this behaviour (still not answered).
Also I get the two popups at every josm start, the first to delete the old certificate and the second to install the new one. I this the wanted behavior?
No, this is a bug.



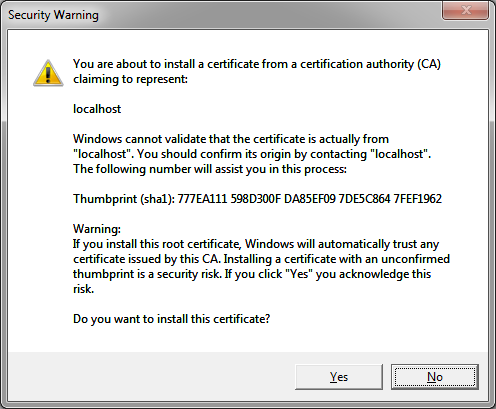
Print Screen of the Security Warning Popup